
Retro — Write-up
Challenge Link: https://tryhackme.com/room/retro
Retro is a box from Darkstar7471 consisting of a virtual machine running a windows web server. We’re tasked with enumerating, gaining access and escalating our privileges. This write up is a snapshot from my full THM Advent Challenges write up.
Let’s get started!
Enumeration:
If you try to enumerate this machine, you’ll notice the first of Darkstar’s little challenges designed to make this more difficult. The VM will not respond to ping requests, and will always appear down if we scan it with Nmap as normal. In order to get any meaningful results, we have to include the -Pn switch in the nmap command, like so:
sudo nmap -Pn -sV -p- -vv <machine-ip>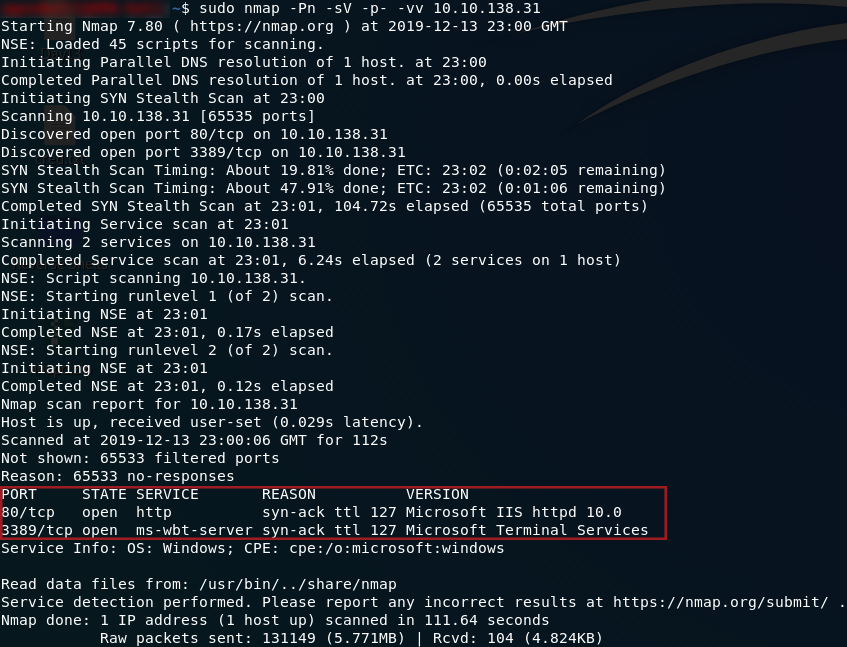
So, we have two ports open: 80 running a HTTP server, and 3389 running an ms-wbt-server. We’ll focus on the webserver first, but we will be coming back to port 3389 later. Head to http://<machine-ip> and we’ll see what we have running:
Huh. The default landing page. Well, there’s gotta be something else lying around here. We’ll use Gobuster to scan the IP and see what other directories are available. It’s worth noting here that the answer is not in the common.txt wordlist. We need to use the directory-list-2.3-medium.txt wordlist to find our answer. This list would take a lot longer to run, but fortunately the directory comes up very quickly, and we can cancel the scan after that:
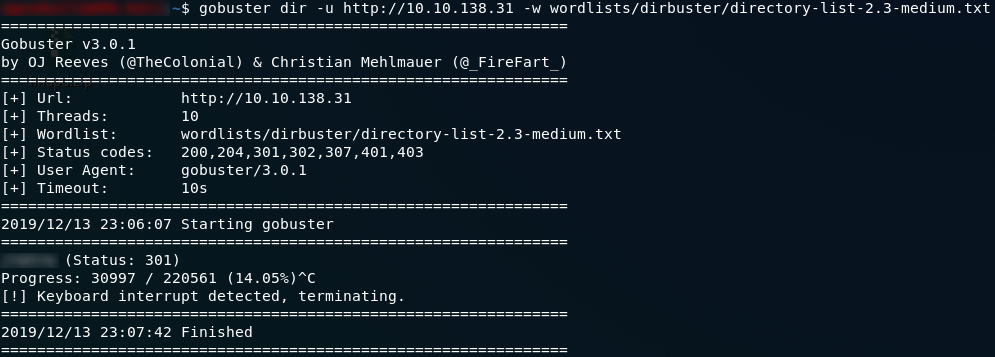
Wonderful. We have the directory where the website is served from, which also gives us our first answer.
If we navigate to the subdirectory that hosts the website, we can see that it’s an… analysis? of old video games. Now, what can we do with this? Looks like all of the blog posts are authored by someone called Wade. Let’s take a look at his account by clicking on his name at the top of any of the posts:
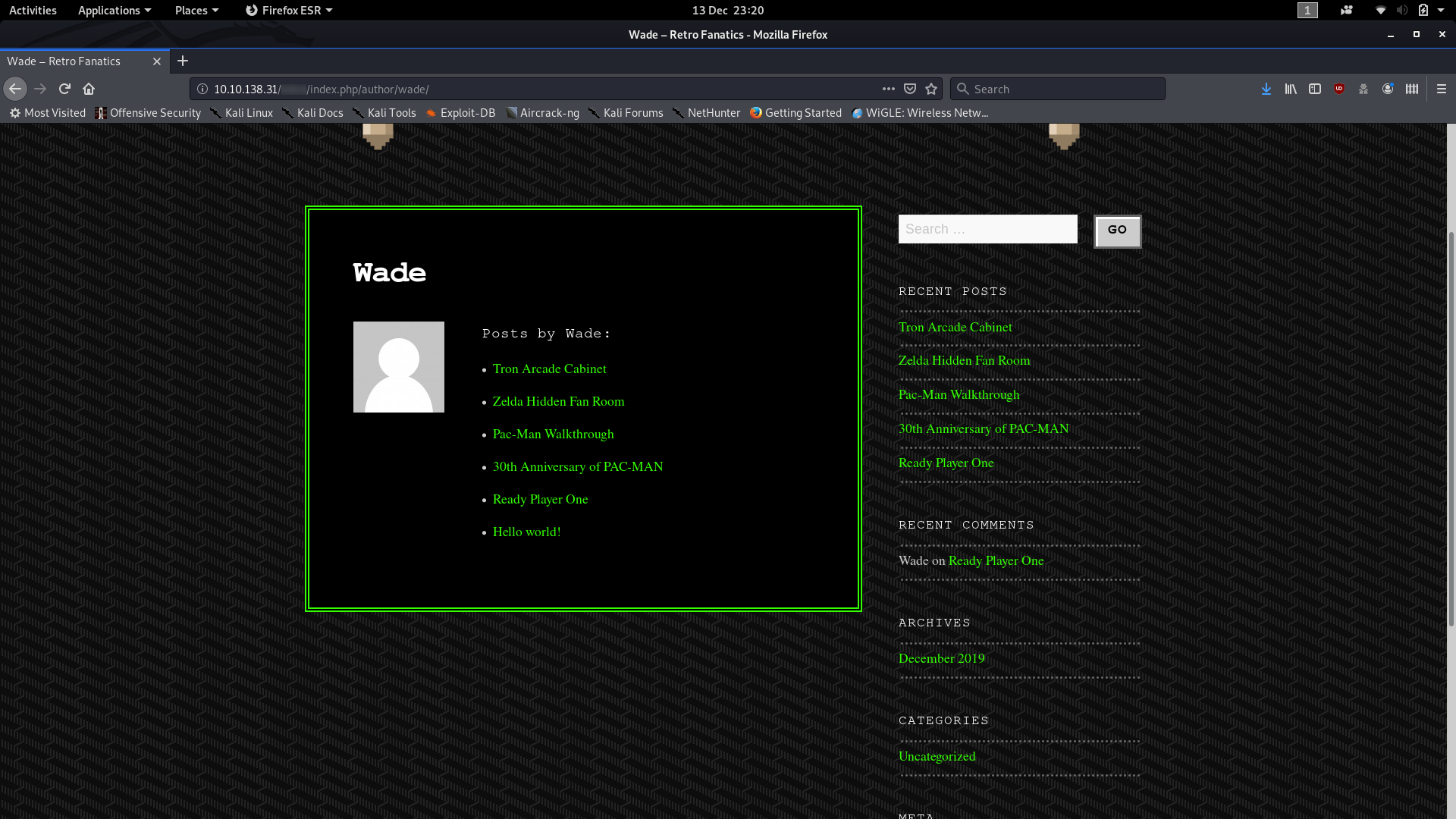
Ok, so we have a bunch of posts, but we’ve already looked through all of them on the homepage — their content holds nothing of interest to us in relation to the CTF; but there’s something else that Wade posted which might be interesting:

I wonder what Wade might have commented?
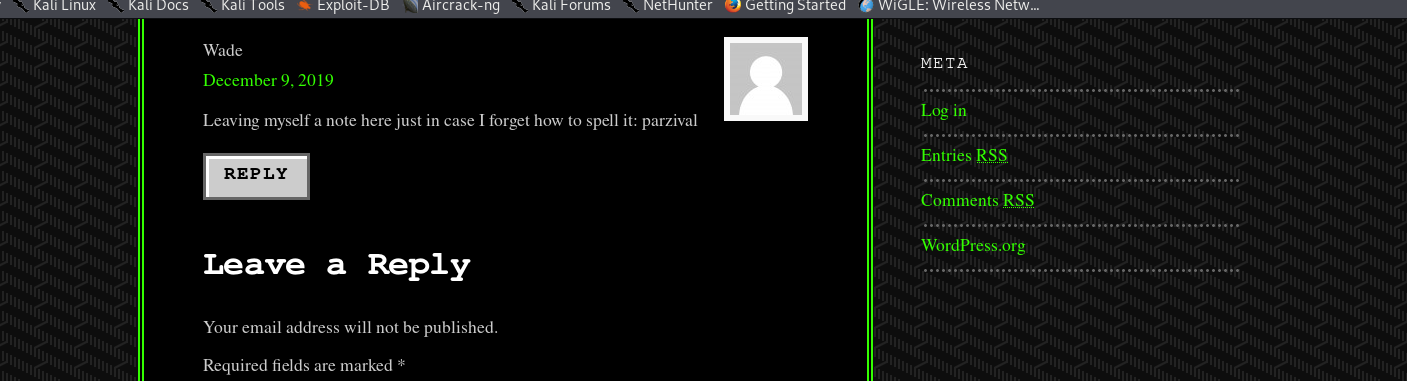
Could that possibly be Wade’s password?
Exploitation:
The eagle-eyed hacker might have noticed that there is a Log in button over on the right hand side of the page. By merit of experience I’m going to suggest that you ignore it for now, although by all means log in with the credentials we’ve found if you’d like. For now though it is the next in a long line of dead-ends that Darkstar has kindly set up for us to fall into.
Instead we’re going to think back to that other port we found in our nmap scan — port 3389, hosting an ms-wbt-server. This port allows us to get a remote desktop session with the target computer, so from here on out we’ll be using a GUI. Due to the windows firewall being a pain in the rear end, rdesktop will not work for this, so I would advise instead using Remmina.
Load up Remmina and use the your remote IP along with the credentials that we found earlier (wade:parzival) to login. You should notice immediately that the user.txt flag is sitting on the Desktop:
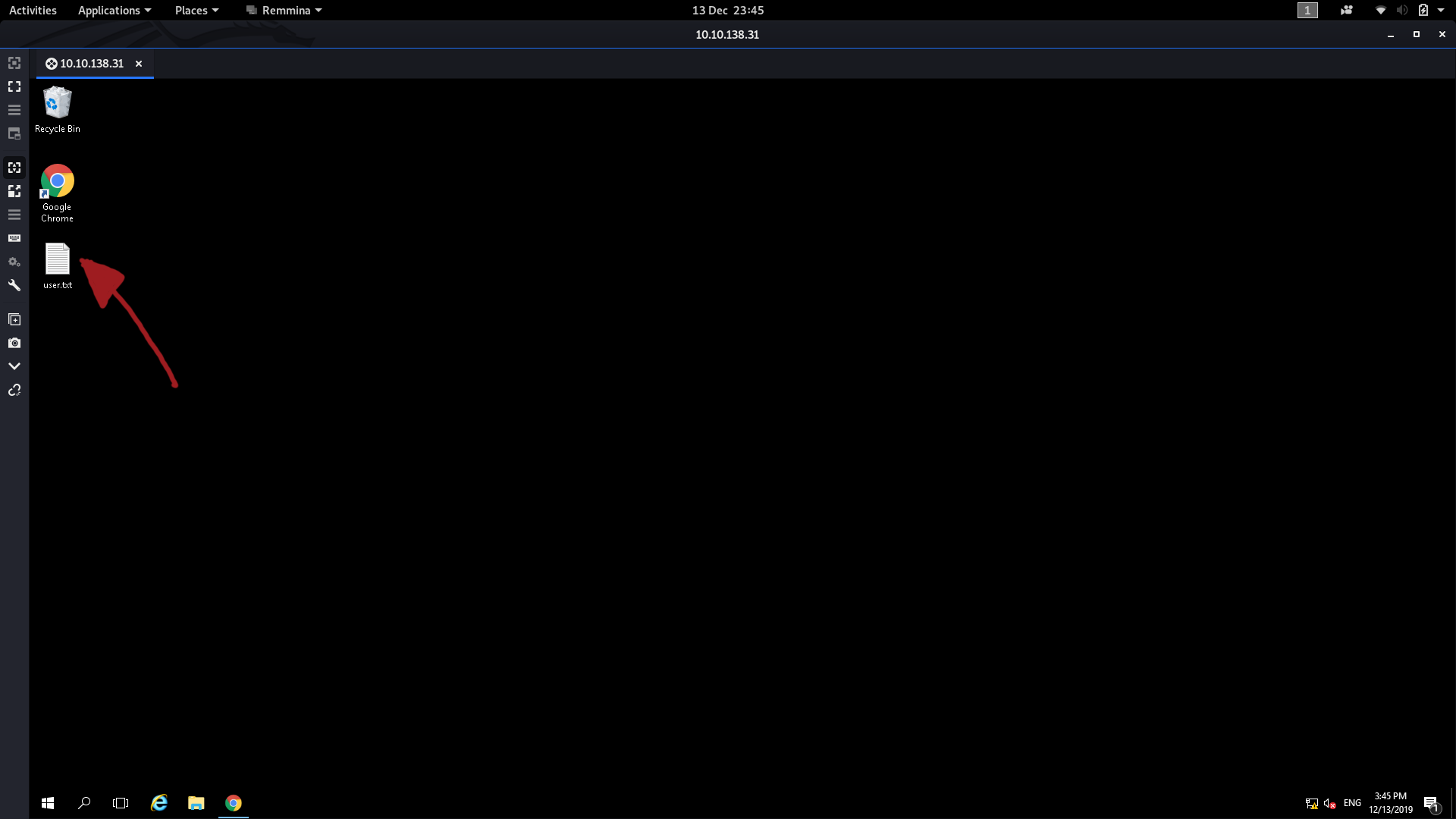
That, obviously, contains the answer to the second question.
Privilege Escalation:
The third question gave a lot of people (myself included) a huge challenge for a very long time.
If we look at the hint for the last question, it tells us to look at what the user was trying to do last time they were logged in. This points us towards the user’s internet search history, so let’s open that up and see what we can find:
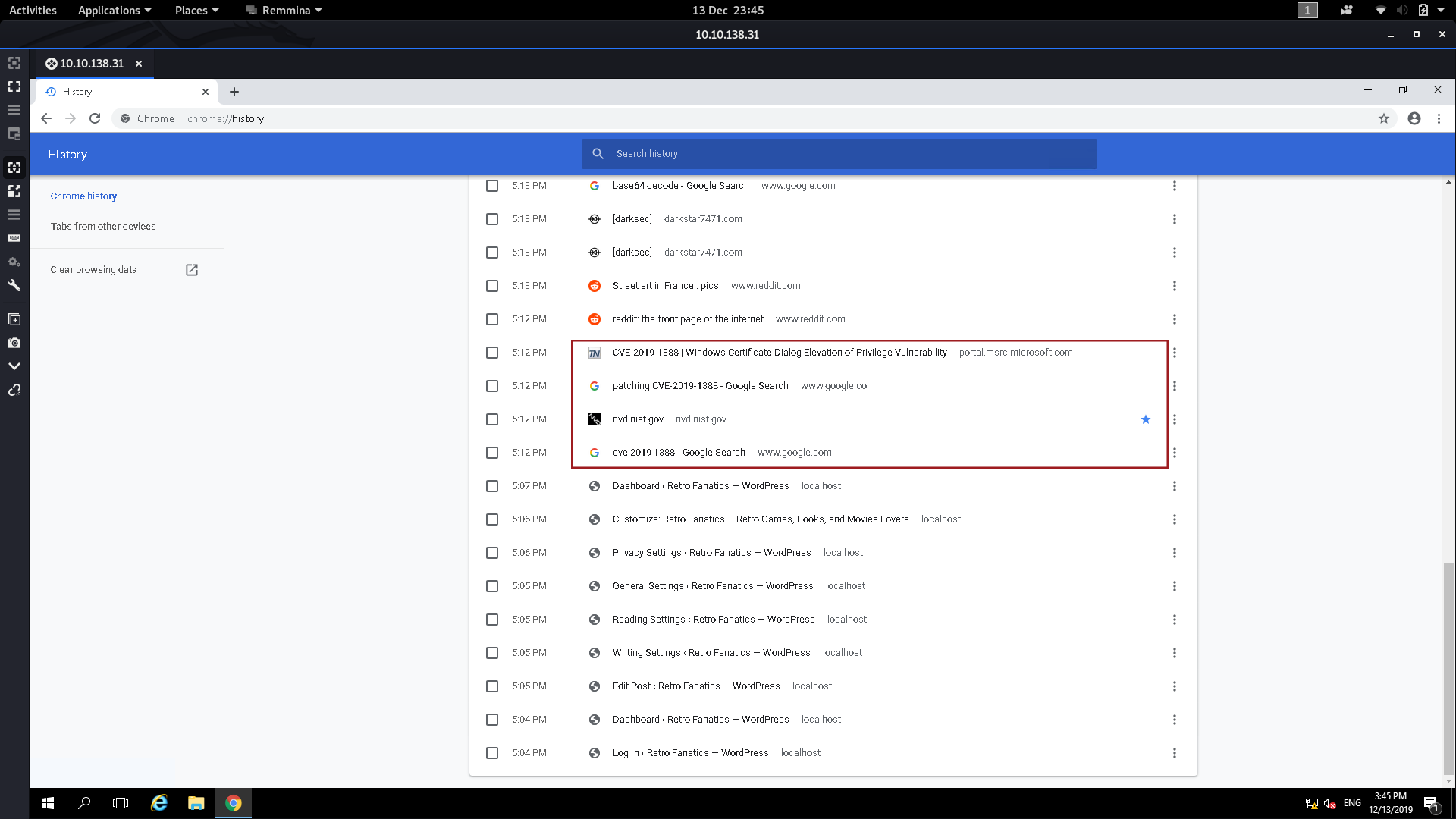
Down at the bottom of the history we can see that the user was trying to figure out how to patch CVE-2019-1388 — maybe this means that the machine is vulnerable to it?
A quick Google search tells us that CVE-2019-1388
involves manipulating a system process into opening a webpage, which we
can then use to get a file dialogue, which we can use to open command
prompt as System. A bit convoluted, but it works.
Specifically what we’re going to be doing is attempting to run a .exe
file as Administrator, then, when it asks for a password, we’re going
to have a look at the certificate of the file. With this particular file
the certificate details contain a link to more information, which, when
opened, spawns a System session of the web browser. Thus if we can open
a file dialogue from this window we’ll be able to open any file as
system including Command Prompt.
Fortunately for us, someone has already downloaded the .exe file we need. They also deleted it, but good ol’ windows has kept it in the recycling bin. The file is hhupd.exe — drag it out onto the desktop and there will only be one thing we need to do before we can perform the exploit.
Start up both Internet Explorer and Google Chrome (I’ll explain why after walking through the exploit), then we’re ready to go.
To carry out the escalation, we first need to right-click on the .exe file and choose to run it as Administrator. When we do we get this window:

Click on “Show more details,” then choose “Show information about the publisher’s certificate.” Another window should pop up — click on the “Issued by” link:
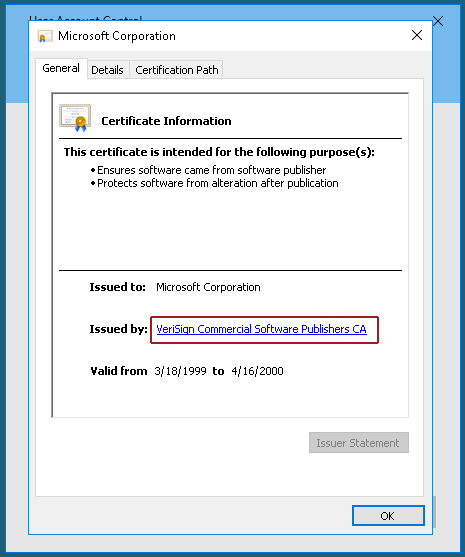
At this point you should be asked to pick a browser — choose Internet Explorer.
A lot of people had problems performing this exploit as (due to an intentionally activated bug in Windows Server 2016), there are initially no options presented to open the link, like so:
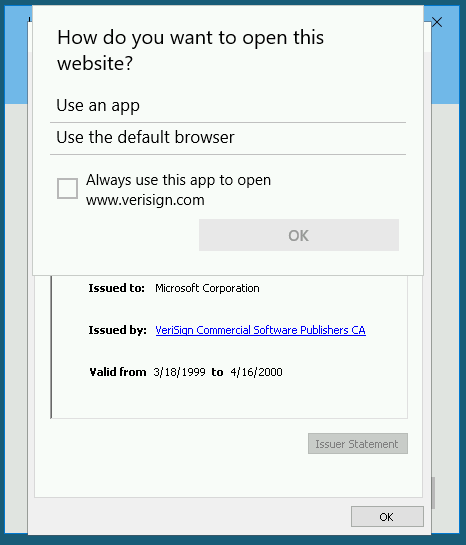
The fix presented by Darkstar is what we did to begin with: initialising both Google Chrome and IE before performing the exploit.
Anyway, exit out of the two windows and we should now have an Internet Explorer window up:

Remember that we aren’t connected to the internet, so the error message is actually fine. From here you can escalate your privilege using either the save file dialogue or the open file dialogue. I’ve used both when testing stuff for this write-up, but for now we’re going to press Ctrl + S to get the save file dialogue open:
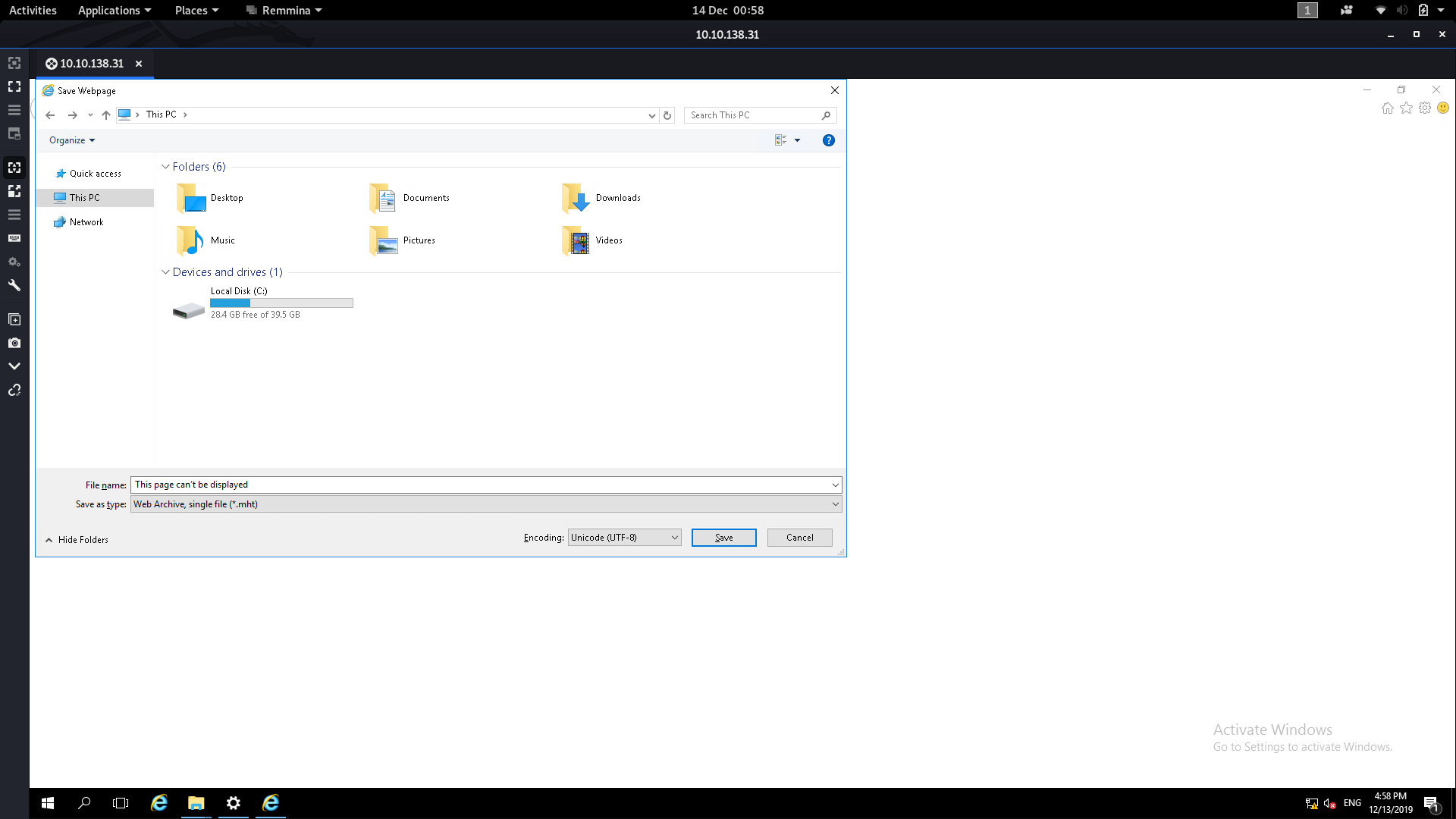
From here we need to navigate to the System32 folder. Type the following into the File Name box then press Enter:
C:\Windows\System32\*.*
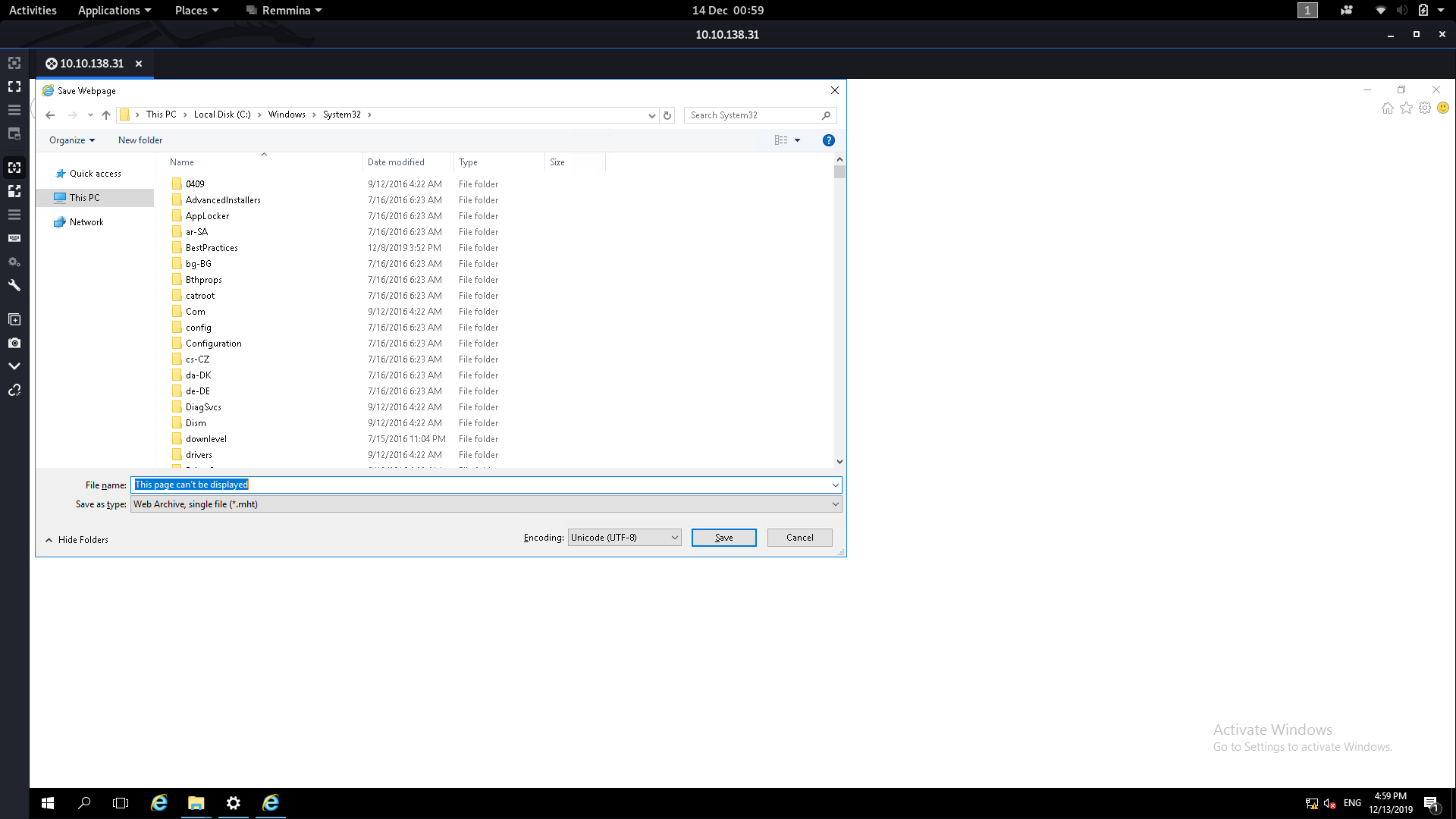
From here we can scroll down until we find cmd :
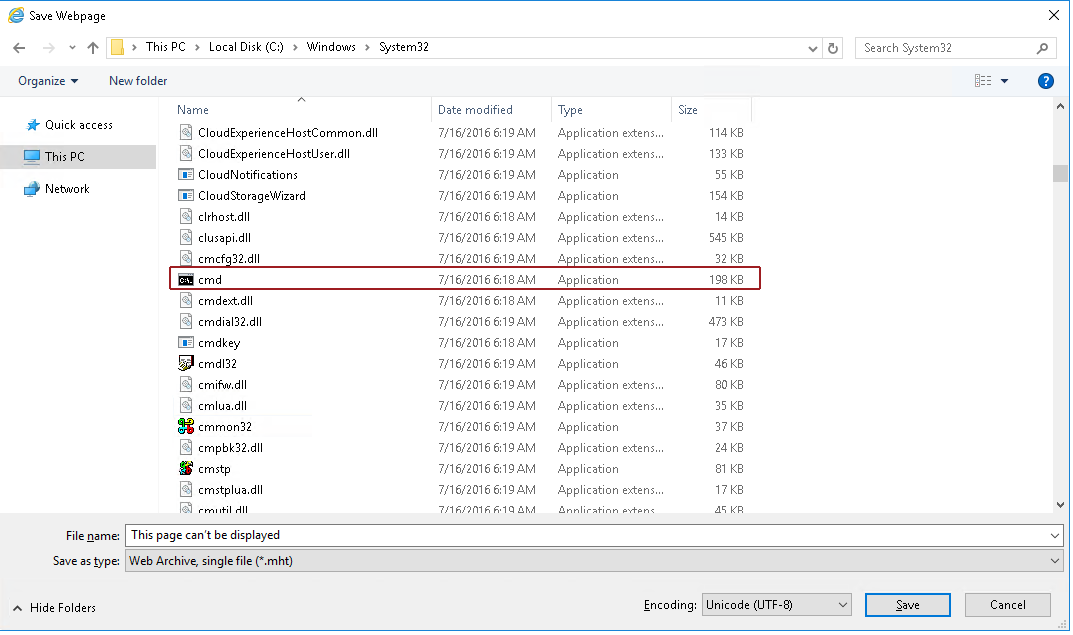
Right click on cmd then click open (no need to use Run as administrator — just open it). We’ll now have a command prompt shell running as System32!
This shell has pretty much the highest privileges on the box, so from here it’s easy to read the flag from the Administrator account:

Thus we now have the answers to all three questions in this room.
*(N.B. It’s worth noting that this escalation can be done using Google Chrome, but as far as I can tell you’re restricted to using the open file dialogue)